
21-C, Zamzama Commercial Lane # 5, Phase V, D.H.A., Karachi 75500, Pakistan.
APIs (Application Programming Interfaces) are critical components that enable various software applications to communicate with each other. However, the increasing reliance on APIs has also opened up new vectors for security vulnerabilities.
Here are some critical API security threats you should be aware of:
Insecure API Endpoints
Threat: Payment APIs without secure endpoints can lead to data breaches. For example, an unsecured API endpoint might not implement SSL/TLS encryption, making it susceptible to Man-in-The-Middle (MITM) attacks where attackers intercept financial data during transmission.
Mitigation: Enforce HTTPS on all API endpoints to ensure data encryption in transit. Utilizing HSTS (HTTP Strict Transport Security) can further enhance security by forcing browsers to use secure connections.
Flawed Authentication Mechanisms
Threat: APIs that rely on weak or improperly implemented authentication mechanisms are prone to unauthorized access. A notable incident involved an attacker exploiting weak API keys in a payment processing API, allowing them to initiate unauthorized transactions.
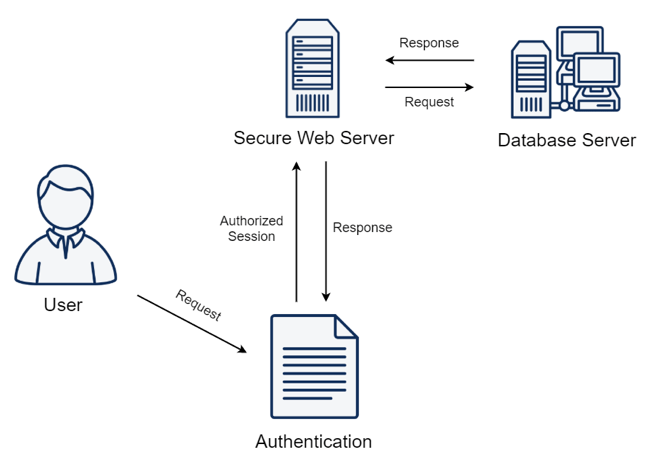
Mitigation: Implement robust authentication protocols such as OAuth 2.0, and require strong, periodically rotated API keys. Additionally, employing API rate limiting can deter brute force attacks on authentication mechanisms.
API Injection Attacks
Threat: APIs vulnerable to SQL Injection or Command Injection can be manipulated to gain unauthorized access to the database or execute arbitrary commands. A real-world scenario involved attackers injecting malicious SQL queries through a payment API’s input field, compromising customer payment information.
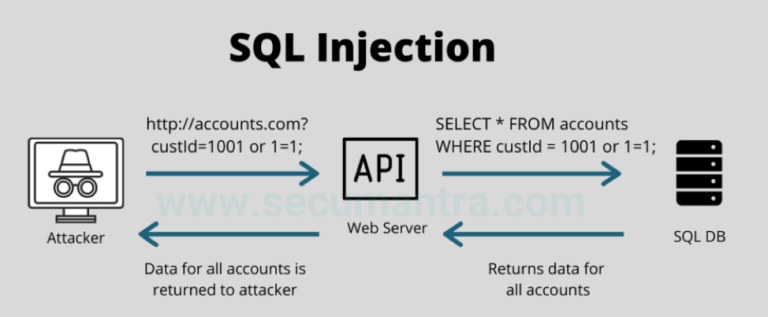
Mitigation: Utilize prepared statements and parameterized queries to protect against SQL Injection. Always validate and sanitize user inputs to prevent Command Injection attacks.
Excessive Data Exposure
Mitigation: Utilize prepared statements and parameterized queries to protect against SQL Injection. Always validate and sanitize user inputs to prevent Command Injection attacks.
Excessive Data Exposure
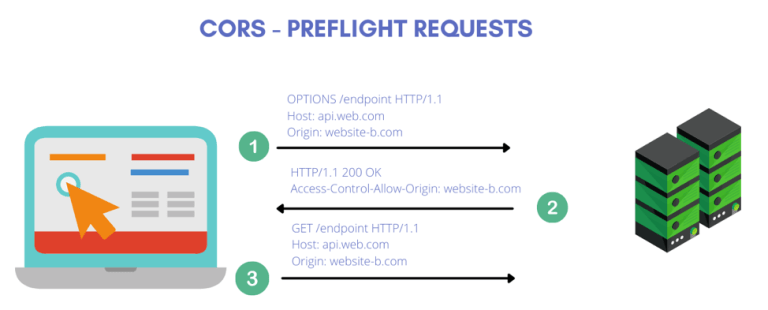
Mitigation: Specify explicit, trusted domains in CORS policies and avoid overly permissive settings. Implement anti-CSRF tokens to protect against CSRF attacks.
Broken Access Control
Threat: Insufficient access control allows attackers to access or modify resources they should not access. An incident occurred where an attacker exploited broken access controls in a payment API to access other users’ transaction histories.
Mitigation: Enforce strict access control measures, ensuring that users can only access resources pertinent to their privileges. Regularly review and update access control policies to cover new API endpoints and functionalities.
Conclusion
The specific vulnerabilities of payment APIs highlight the need for a vigilant, security-first approach to API development and deployment. By understanding the nuances of these threats and employing comprehensive mitigation strategies, businesses can secure their payment processing systems against exploitation, safeguarding financial transactions and customer data.
(+92) 21 3537 3337
support@dunicot.com
At Dunicot, we specialize in advanced cybersecurity services tailored to your business needs. Our core business mission is to guide our client’s data security practices to a state of perfection, enabling them to be ahead of the curve.
Pakistan | USA | Canada | Singapore | New Zealand | Africa | Saudi Arabia | UAE | Qatar

