
21-C, Zamzama Commercial Lane # 5, Phase V, D.H.A., Karachi 75500, Pakistan.
Introduction to Security and Privacy Threats in Web3
Web3 stands out as a groundbreaking advancement, integrating decentralization with user preference. However, this new wave of internet innovation brings a host of security and privacy concerns that must be addressed. Web3 poses many security and privacy risks, and you must be aware of these risks to navigate its challenges effectively.
This article will explore the main security and privacy threats present in Web3 and recommend strategies to address these concerns comprehensively.
Exploring Web3 Security and Privacy Threats
Hacking and Phishing
These attacks exploit vulnerabilities in dApp code or infrastructure to gain unauthorized access to private keys, wallets, and sensitive data.
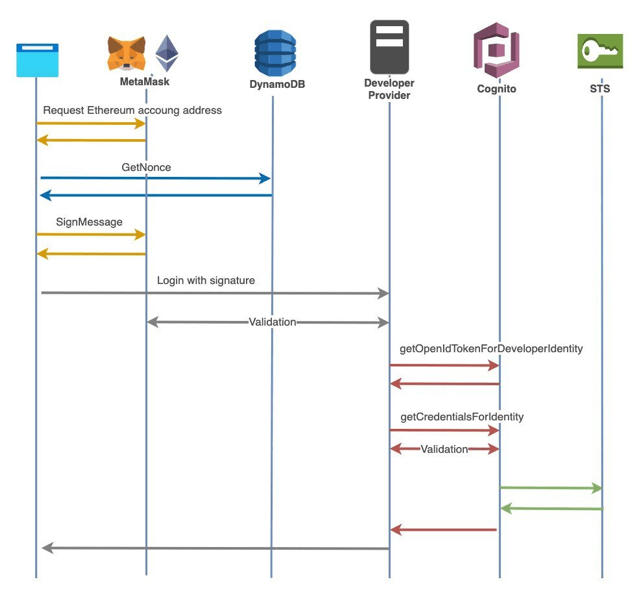
For example, malicious smart contracts or misleading interface elements can be used to trick users into unauthorized transactions.
Smart Contract Vulnerabilities
Smart contracts are fundamental to Web3 but can contain flaws leading to unintended actions and potential loss of funds.
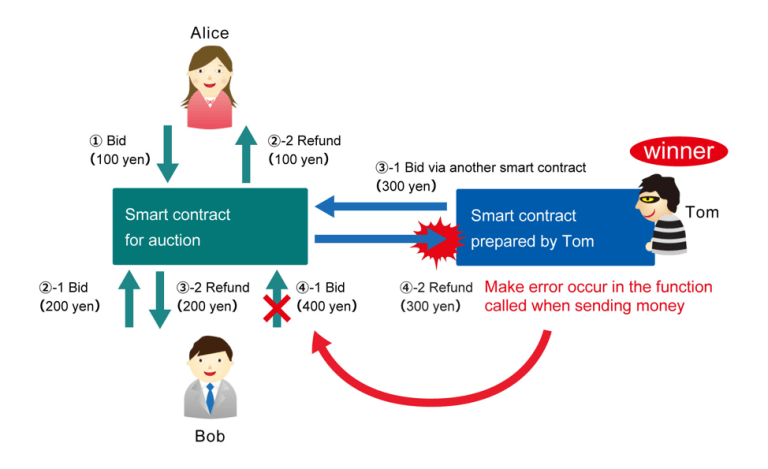
For instance, A smart contract fails to validate input correctly, allowing attackers to withdraw funds repeatedly.
Logic Vulnerabilities in dApps
Vulnerabilities such as faulty backdoors or logic flaws in decentralized applications can lead to security breaches. An example is a decentralized finance (DeFi) application that calculates transaction fees incorrectly, enabling exploitation for unintended profit.
Supply Chain Attacks
Targeting specific components within the application, such as compromised open-source libraries, that can be used to inject malicious code.
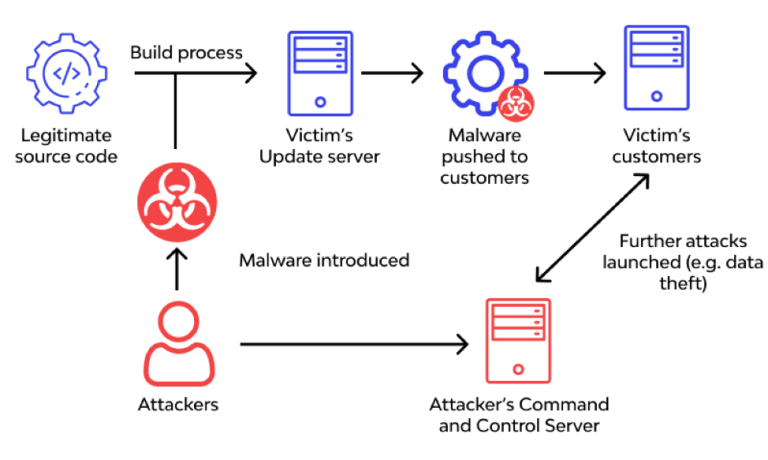
For instance, An attacker submits a malicious update to a widely used library, compromising all dApps that depend on it.
Zero-Day Exploits
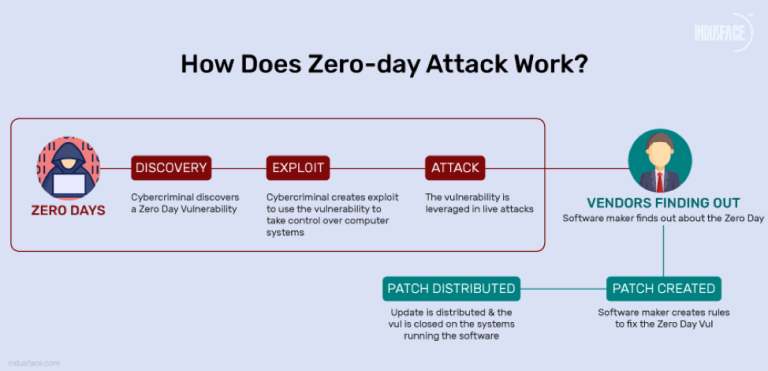
These exploits take advantage of vulnerabilities that are not yet known to the community or developers. For example, a zero-day exploit in popular blockchain client software could allow attackers to bypass network security and perform unauthorized actions.
Metadata Leakage
The metadata attached to transactions can reveal sensitive information about users, despite the immutability of blockchains. An example is analyzing transaction times and amounts to deduce the identity of parties involved in a transaction.
Blockchain Analytics: While useful for data-driven personalization, it can inadvertently expose sensitive information. Example: Using transaction data to track the financial activity of users without their consent.
Proactive Measures for Enhancing Web3 Security
Conclusion
The rapid adoption of Web3 technologies necessitates a vigilant approach to security. By understanding the complex landscape of threats—from hacking and phishing to smart contract vulnerabilities—users and developers can better prepare to counter these risks. Implementing robust security measures and fostering a culture of continuous education and improvement will be key in advancing Web3 technologies safely and sustainably. As the sector continues to evolve, proactive security practices will not only protect but also enhance the reliability and user trust in decentralized applications.
(+92) 21 3537 3337
support@dunicot.com
At Dunicot, we specialize in advanced cybersecurity services tailored to your business needs. Our core business mission is to guide our client’s data security practices to a state of perfection, enabling them to be ahead of the curve.
Pakistan | USA | Canada | Singapore | New Zealand | Africa | Saudi Arabia | UAE | Qatar

